Months of grueling dev work: wrangling Dockerfiles, Kali’s rolling release breaking our build for the umpteenth time, naming all our internal tools after cool birds…. And it’s finally left the nest, ready for the public.
A quick recap on who and what we are
We at Dev Aviary are a team of two bringing our knowledge of cybersecurity and pedagogy together to create a fun, interactive learning experience for an expanding array of topics in cybersecurity (currently XSS and SQLI). We focus on practice over pure theory, especially practice with real-world scenarios.
That’s why we designed our courses as a series of practical labs tasking you with enacting each exploit we teach. This includes:
- simple exercises
- entire themed “playgrounds” (fun scenarios such as a web app featuring multiple vulnerabilities)
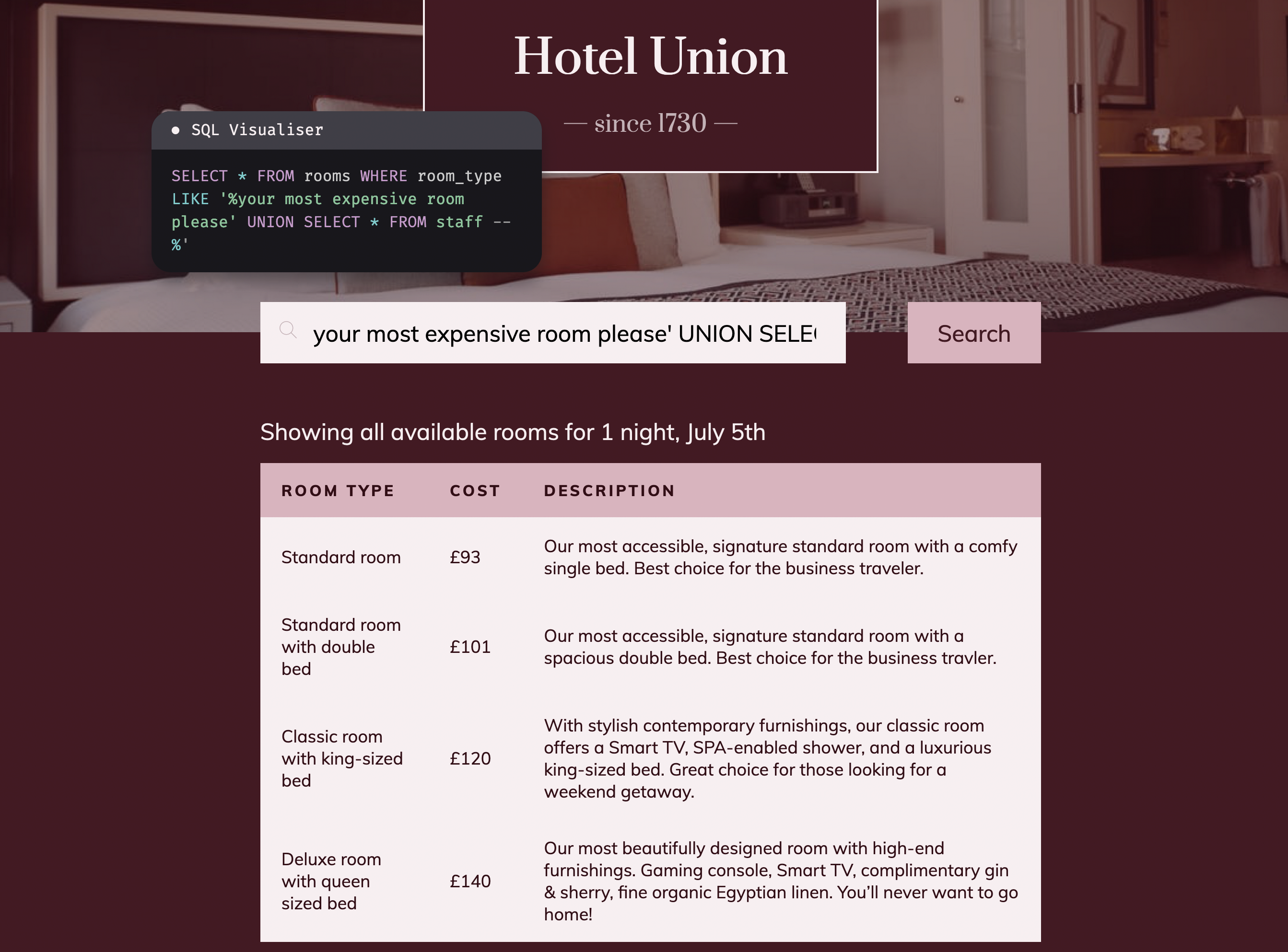
- actual real-world case studies pulled from vulnerable versions of open-source software (for example, Gitea’s version 1.12.0)
We’re reinforcing learning by providing two separate labs per attack taught. All our labs are accessible in the embedded VM (right in the browser!) running Kali Linux loaded with tons of pentesting tools, because it’s much more convenient than having to wrestle with VMs on your own. And there’s plenty of guidance and optional hints for when you need them.
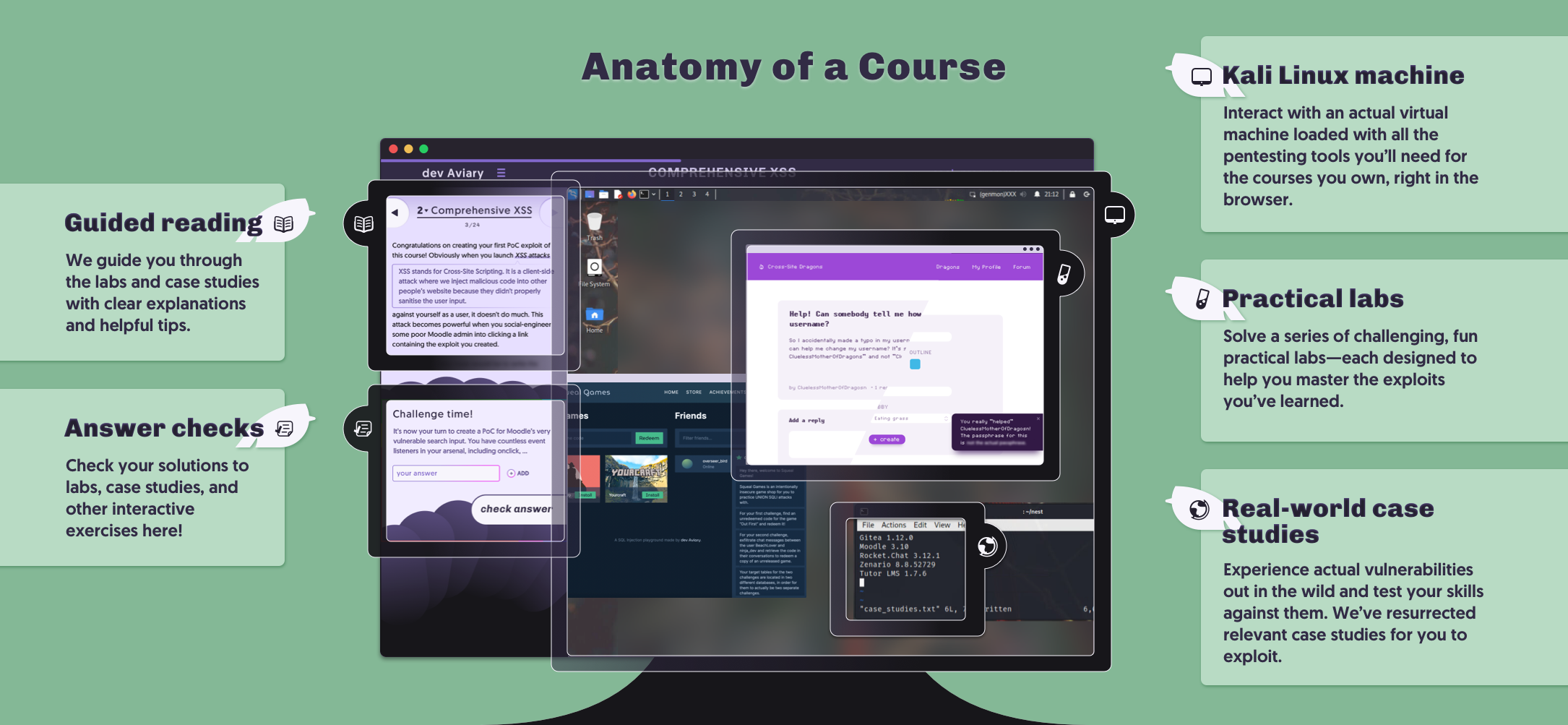
There are tons of cool learning features we’ve got planned, like learning tracks (a series of related courses that build on each other), challenge labs for extra practice, discussion forums, and even a rankings/point system to gamify your learning experience. But for now, we have finally got a working foundation. Let us tell you about the endless trials and tribulations we faced to get here.
The circles of dev hell
Developing on the bleeding edge is not what we’d advise but absolutely necessary to support the ambitious vision we had for Dev Aviary. Here’s a checklist of some issues we had to overcome:
- install VS Code for non-Vim, non-Emacs users — but of course VS Code is built on Chromium, whose newer versions are picky about whether it’s run by root
- twiddle with routing rules so you can’t touch what we don’t want you to touch while still allowing some essentials within arm’s reach (a frantic Traefik docs read later)
- forge a two-way copy/paste (it’s a little janky and still needs love)
- painstakingly build deprecated vulnerable versions of software (and hand-fix the code that was buggy in the wrong way) for our real-world case studies
- rebuild said vulnerable versions of software whenever Kali’s rolling release broke the build
- provide a safe zone — a persistent volume where you can store files so they’re not swallowed up by the void when your machine is rebuilt with new courses
Not just the labs themselves, but our internal tools and everything surrounding the web app posed hellish challenges:
- automate the slapping together of labs and playgrounds into one unified course, with the help of our internal tool “corvid” (caw caw 🪶)
- flowchart our weird system of lab host allocation
- pivot to an alternative frontend build tool for the second time, because Snowpack has just been made obsolete — wait, we’ve still got to do this
Whydunnit
Dev Aviary was born out of frustration at existing cybersecurity learning resources and a desire to provide something better. Our cybersec expert co-founder personally crawled through the wasteland of odd YouTube video tutorials, DIY vulnerable boxes based on VM images downloaded off dying websites, and outdated books lacking any form of practice.
Sure, there are (expensive!) university degrees and courses for enterprise if that’s in your price range and accessible. Our co-founder opted to pay more reasonable amounts, but found the explanations less effective when delivered as a stack of slides with little formatting, copy/paste disabled, typos galore, and sometimes condescending support…. At least the certs earned are recognized somewhere. For practice, there are plenty of capture-the-flag-style boxes.
But what we find most effective are non-contrived real-world scenarios. Even better if we can eliminate the struggles and incompatibility issues of setting up intentionally vulnerable servers, configuring networking for the attacker machine, and replicating the intended attack. It was this desire to modernize cybersecurity education that birthed Dev Aviary.
If you feel the same way we do about learning cybersecurity, please do check us out :)
If you’d like to help out and be a beta tester, in return we offer a 70% discount for our courses. Drop us a message here here if you want to beta-test our courses!